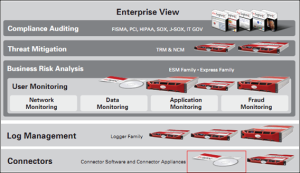
 Security Information and Event Management (SIEM) is one of the most vital elements in IT Infrastructure landscape management to ensure secured and healthy business platform. Broad adoption of SIEM technology is being driven by the need to detect threats and breaches, as well as by compliance needs. Early breach discovery requires effective user activity, data access and application activity monitoring. This practice encompasses advance security monitoring, advance analytic, adequate intelligence, matured process set up to respond fast for any security breach while recovering data with zero to minimal disruption. We have been hearing certain terminologies in the security threat world such as “Zero day vulnerabilities”, “BotNet”,”DDoS attack”, “Brute Force attack” etc. We have had numerous security incidents causing millions of millions of dollar impact, damaging business brand, prestige and loyalty. I don’t intend to give a big explanation of all these terms in my blog today, one can easily google, go to Wikipedia or refer my prior article on this topic @ http://www.techmanthan.com/index.php/2015/07/19/it-security-race-between-it-evolution-and-security-threat/ and get detail. I intend to cover smart SIEM while emphasizing the need to have culture and intense process set up around and security, confidentiality and privacy in IT or any enterprises that caters to transactional data involving financial, health, defense or anything that has got element of privacy. Instead of continuous security awareness program including enterprise wise security policy updates, modern security infrastructure availability in both traditional and public cloud enabled DC, complex password compliance etc. security threat continuous to increase with new attributes and styles thereby requiring both IT and business ecosystem to intensify the culture of security by investing into innovative solution around SIEM and develop proactive and analytical solution across network and end point devices. Threats are becoming more sophisticated by adopting advanced technique to compromise only fewer hosts giving less trace for identification as compared to what used to be before by compromising massive number of hosts and giving easy pattern to derive signatures. Attackers are leveraging the inbuilt tools rather than introducing new executable codes to spread out while managing to stay obfuscated and establishing approved accounts to attack IT ecosystem in newer ways. In the era of cloud & virtualization such spread becomes far easier and can result more devastating & detrimental to the security, privacy & confidentiality set up while hugely risking all range of business establishment such as IT, BFSI, Health industries.
Security Information and Event Management (SIEM) is one of the most vital elements in IT Infrastructure landscape management to ensure secured and healthy business platform. Broad adoption of SIEM technology is being driven by the need to detect threats and breaches, as well as by compliance needs. Early breach discovery requires effective user activity, data access and application activity monitoring. This practice encompasses advance security monitoring, advance analytic, adequate intelligence, matured process set up to respond fast for any security breach while recovering data with zero to minimal disruption. We have been hearing certain terminologies in the security threat world such as “Zero day vulnerabilities”, “BotNet”,”DDoS attack”, “Brute Force attack” etc. We have had numerous security incidents causing millions of millions of dollar impact, damaging business brand, prestige and loyalty. I don’t intend to give a big explanation of all these terms in my blog today, one can easily google, go to Wikipedia or refer my prior article on this topic @ http://www.techmanthan.com/index.php/2015/07/19/it-security-race-between-it-evolution-and-security-threat/ and get detail. I intend to cover smart SIEM while emphasizing the need to have culture and intense process set up around and security, confidentiality and privacy in IT or any enterprises that caters to transactional data involving financial, health, defense or anything that has got element of privacy. Instead of continuous security awareness program including enterprise wise security policy updates, modern security infrastructure availability in both traditional and public cloud enabled DC, complex password compliance etc. security threat continuous to increase with new attributes and styles thereby requiring both IT and business ecosystem to intensify the culture of security by investing into innovative solution around SIEM and develop proactive and analytical solution across network and end point devices. Threats are becoming more sophisticated by adopting advanced technique to compromise only fewer hosts giving less trace for identification as compared to what used to be before by compromising massive number of hosts and giving easy pattern to derive signatures. Attackers are leveraging the inbuilt tools rather than introducing new executable codes to spread out while managing to stay obfuscated and establishing approved accounts to attack IT ecosystem in newer ways. In the era of cloud & virtualization such spread becomes far easier and can result more devastating & detrimental to the security, privacy & confidentiality set up while hugely risking all range of business establishment such as IT, BFSI, Health industries.
SIEM Context
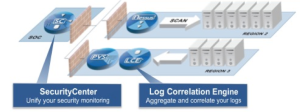
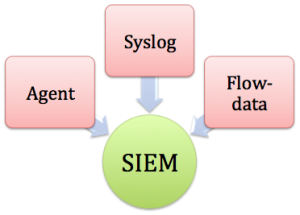
Before going further let me give quick context, SIEM technology aggregates event data produced by security devices (AV, Symantec processes etc.), network infrastructures (Switches, routers, packet filter, packet detection system, monitoring tools such as Spectrum, Netscout etc.), systems and applications. The primary data source is log data, but SIEM technology can also process other forms of data, such as NetFlow, sFlow and packet capture. Event data is combined with contextual information about users, assets, threats and vulnerabilities. The data is normalized, so that events, data and contextual information from disparate sources can be correlated and analyzed for specific purposes, such as network security event monitoring, user activity monitoring and compliance reporting. The technology provides real-time security monitoring, historical analysis and other support for incident investigation and compliance reporting.
Network Vs. End Points
Security landscape has been evolving from end point detection to network devices to the packets filtering, inspection and detection. There has been slew of tools and applications by vendors such as AccelOps, SolarWinds, Splunk, NetWitness NextGen, Nagios, Argus etc. to monitor hosts, resources, applications and network components viz. SNMP, HTTP, ICMP, Packets, capacity, flow rate etc. and have been able to address the security related incidents to a great deal. Statistically, over 60% data breaches have happened on endpoints; however, many enterprises still fail to deploy response solutions that can deliver actionable visibility and intelligence down to the endpoint, various organization have been investing security dollars more into their network than end points. In my opinion, security approach should lay emphasis more on the end points than the corporate network. It is always end points that get compromised first if this doesn’t have strong layer around. Today, employees are carrying multiple devices (BYOD) viz. mobile, tablet, laptops etc. as well as are working remotely while staying connected with other networks apparently with less stringent firewall policy exposing themselves to the world of threats. Attackers have been always researching and finding ways and new methods to compromise end device to further spread and contaminate rest of IT elements.
The endpoint is the target of attackers because this is where the valuable data resides. Enterprises must identify key data, assess the probability of that data being targeted by attackers, estimate the business impact of that data being compromised, and determine where that data is located. Apart from Antivirus software we need to have the set up to continuously monitor, detect, prevent and respond rapidly at the endpoints.
Organization must depart from reactive & adhoc incident response solution to formal and matured framework to enable fast decision system, quick and proactive cost effective security incident solution. Responders also should look to optimize their enterprise’s security so that any response is reliable, predictable and adaptive to the changing threat landscape. I am using an image from “bit9.com” reflecting upon next generation Endpoint and server security.
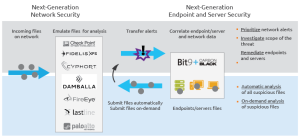
Courtsey: www.bit9.com
Data Collection over Detection
Data collection process should be in-built and continuous whether threat is there or end point has been compromised or not? If compromised, we can instantly leverage data and discover the pattern and trend while instituting solution to prevent such threat from occurring in the future. For ex. Set up a process or tool that enables enterprises to prepare for a breach by proactively automating and continuously recording the critical data before the moment of compromise and thus reduces the dwell time of attackers exponentially by enabling us to dive into the response immediately and recover faster. SIEM practice is continuously evolved by the need to analyze security event data in real time for internal and external threat management, and to collect, store, analyze and report on log data for incident response, forensics and regulatory compliance.
Increase Threat Intelligence
Many organizations lack the necessary threat intelligence to help them fully detect and classify attacks as they happen. Threat intelligence should be a valuable part of any detection or response solution. Without threat intelligence, enterprises can lose valuable insight into threats as they arrive in their environment. Organizations need to focus on solutions that can accelerate the discovery of advanced threats as opposed to those that just produce more detection events. Fixing this will exponentially reduce the dwell time of threats in an environment by accelerating investigations to minimize the scope of an attack. Unlike, most of current detection solutions that filter out endpoint visibility when detecting threats in an environment, we should look for solution that can aid analysis and increase intelligence. The current traditional solution typically provide the specific instance of the attack and its compromised host, but by filtering out endpoint visibility, loses sight of lateral movement, root cause and the entire scope of the attack during an investigation. Our goal should be to understand the scope and root cause as confidently and quickly as possible. For Example, by proactively recording and maintaining the relationships of every file execution, file modification, registry modification, network connection, cross-process event and executed binary we can obtain conclusive and confident insight into the full scope of an attack—enabling us to respond rapidly.
Enterprises need security solutions that offer the ability to integrate with a wide range of threat intelligence feeds, as well as enable to add their own custom feeds. This affords businesses the opportunity to incorporate threat intelligence feeds not initially offered by a security solution.
Apply & Calibrate Analytic algorithm
As Data Science teaches us to first create a prototype/algorithm and train the same with training data before applying the model to live data, same principal applies here in maturing up the threat intelligence. While we capture data continuously and apply detection algorithm to identify threat, we need to calibrate the algorithm as and when threat occurs while maturing up the detection model or algorithm. Proactively capturing data is starting point, and one needs to emphasis “what” part, meaning what to do with the data. Applying threat intelligence on top of continuous endpoint visibility enables us to detect attacks in real time and prioritize investigations. Our analytic algorithm is a powerful element of the comprehensive security solution that offers the ability to detect based on entire attack processes, network activity, threat intelligence, attack behaviors and more—not just individual events. Threat intelligence and increased end point visibilities are the powerful combination that enhances our detection capabilities by delivering actionable alerts to reduce alert fatigue. By automating both the data collection and applied threat intelligence process responders also gain instant insight when diving into an investigation.
Instant response while reading continuously
We must develop ability in the solution set up to isolate the bug and/or its host and quarantine them from rest of the system. By automating the tedious and time-consuming data acquisition process and layering threat intelligence on top of that visibility, we should be able to roll back to a point to understand the root cause. By understanding the context and relationships within the collected data, we should perform surgical investigations to identify deleted payloads, lateral movement, malicious outbound connections, and more to identify every step, move and behavior of an attack. This enables responders to see the entire kill chain of an attack in seconds to fully scope the environment and instantly isolate, contain and remediate impacted machines. Once a threat is identified, response teams need to be able to drive action on those impacted endpoints. Many security teams, however, are leveraging multiple tools to identify, respond and remediate threats from their environment. By leveraging a recorded history, security teams can understand the entire scope of an attack, narrow their focus and then drive action on those endpoints. Through one sensor and console, responders can disrupt threats by isolating and containing impacted endpoints. This affords responders time to thoroughly examine those endpoints—such as identifying all currently running processes, registry settings, archiving all session data and retrieving files from a remote host—without fear of the attack spreading. Attackers can also remediate threats by killing live attack processes, changing registry settings, removing files and validating the success of that remediation.
Summary
We need to design a comprehensive smart SIEM solution that stores events preceding any breach, feed into analytic, enrich the pattern recognition or detection algorithm while integrating with callout, notification or response process. The solution must continue to evolve following learn and update as you go approach. It must also give continuous endpoint visibility so that responders can detect, respond and remediate in seconds. The goal should be to evolve, adapt and strengthen prevention and detection solutions moving forward. The solution must reduce the cost of blind re-imaging by only responding to affected endpoints, rather help enterprises immediately learn from their investigations to improve their threat prevention, detection and response in the future. Enterprises are constantly transforming embracing different needs arising out of merger & acquisitions, Policy & Compliance adherence, Infrastructure consolidation, Digital programs, SMAC & IoT and various other advancement & modernization drive from all corners continue to challenge security landscape in IT. The need is to accept that security threat continues to loom and we must include SIEM as an element into IT lifecycle starting from business need to technical requirement to testing to the implementation and finally into the production support phase while creating an instant robust alert response system. IT and business must create a joint team to see and identify security threat from each other and connect to the solution. My approach through this blog is to re-emphasis preventive technique and adequate alert mechanism must be at the core of any product solution, and I am sure with ongoing security research & innovation, IT transformation, process engineering and security in our IT mainstream culture, we shall be seeing reduction of breaches in coming months and years. Let’s stay secure and attentive while following best practices, sharing leanings, increasing awareness and last but not the least following our corporate security policy religiously.